Cyber Threat Intelligence
Stay vigilant, react fast, and anticipate everything with your entire cyber intelligence workflow on one platform.
Messy and missing data, poor communication, and incomplete analysis mean threat actors slip through your fingers. And jumping between multiple platforms to gather, analyze, visualize, and report on data only slows you down further.
But Falkor makes it easy to stay light on your feet – and one step ahead.

How cyber threat intelligence teams use Falkor
Collaborate
It takes a village to prevent a cyberattack which means sluggish email comms and incomplete reports sent out too late are out.
Falkor empowers SOC analysts, threat hunters, IT teams, and executives to communicate, analyze, and upload data on one platform, so everyone has the full picture. Set goals, share reports, and update team members instantly, whenever you need to.
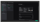
Manage
To preempt threat actors, you need to see everything. But it’s easy to lose track of what you know, what you’ve already done, and what you still need to discover.
Use advanced knowledge and case management systems to find the data you need, and then track every upload, analysis, and evolution in your case.
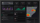
Analyze
When you’re buried in disorganized, unstructured, and irrelevant data, it’s easy for threat actors to fly under the radar.
Powerful data analysis leaves potential threats with nowhere to hide. In-depth visualization tools let you see your data from every angle.

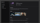
Act
Threat actors move fast. You need to move faster.
Threat response, investigation, and remediation time is cut down from hours to minutes. Insights are uncovered faster with powerful data analysis and visualization tools. Threat indicator reports are generated and disseminated instantly.
How Falkor can enhance your investigations
Analyze anything with leading API integrations that make insights from any data source – MSSP reports, IoCs, SOC alerts, and more – effortless.
Uncover hidden connections with advanced data visualization tools that help you find links between cases, create profiles of bad actors, and analyze data from every angle.
Collaborate securely with iron-clad, permission-based access for everyone on your case – whether they’re a member of your team or an external agency.
Take a bird’s-eye view with customizable dashboards for managers and team members that show you everything you need to know – or set you up to dive into the details.

