Trust & Safety Investigations
One platform for every element of your Trust and Safety investigations: analyze data, explore how bad actors are connected and violating content is distributed, collaborate with other relevant teams, track the course of your investigation, and share meaningful reports with Law Enforcement from one centralized analyst OS.
The purpose of Trust and Safety investigations is to detect and eliminate online harm while ensuring the safety and positive user experience on your platform.
But the field of Trust and Safety is still in its infancy – which means platforms, vendors, and analysts don’t always have the necessary tools they need to properly investigate and respond to threats.
That’s where Falkor steps in.

How Trust and Safety analysts use Falkor
- Child Safety (CSAM, CSEM, Grooming)
- Fake accounts (Spammers, Scammers, Bots, Trolls)
- Threats (Blackmailing, Sextortion, Catfishing, Extortion, Doxxing)
- Bullying, Harassment, Racism, Targeted Hate Attacks
- Toxic content, Animal Cruelty
- Misinformation and Disinformation
- Cyberstalking
- Self-harm communities
- And many more
Knowledge and case management
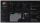
Analysis
Keeping platforms safe means working with a sea of data. With Falkor, you can stay afloat and easily see the full picture of your investigations – or dive into the details. Whatever your investigation needs.
In Falkor, you can explore connections between users, chase leads, enrich your understanding with internal and external data sources for new leads, and analyze data from every angle in a purpose-built environment.
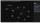
Collaboration
Siloed data might feel more secure, but it also reduces data visibility and accessibility – and stifles collaboration, too.
Falkor gives you a platform where your team can work together securely and in compliance with regulations, so you can share up-to-date data, updates and insights with all stakeholders.
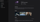
How Falkor transforms Trust and Safety investigations
Ensure the integrity of your platform, services, and user base by creating strong and proactive investigative workflows.
Protect your user base from threat actors that spread harmful content and target user assets.
Automate your on-platform and off-platform investigations with an advanced analytics system.

